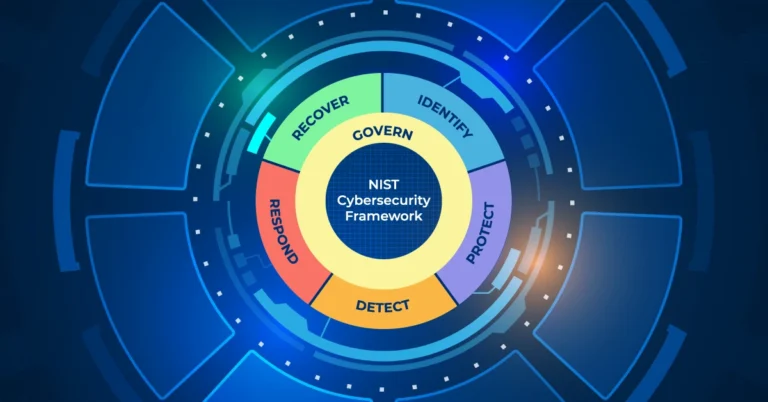
ecrypto1.com Crypto Security: Hidden Threats Most Traders Miss in 2025
Crypto investors lost over $4.3 billion to wallet breaches and protocol-level hacks in 2025’s first half. This massive loss shows why ecrypto1.com’s crypto security has become vital for traders. The digital world has turned more dangerous as social engineering scams targeting token holders jumped 76% this year. Many investors still don’t know about the hidden…