Zryly.com Cybersecurity: Why Hackers Can’t Break Through Our Shield in 2025
Zryly.com cybersecurity delivers a resilient defense against modern threats as cyberattacks evolve into sophisticated operations capable of costing organizations millions of dollars. Ransomware-as-a-service (RaaS), supply chain intrusions, and zero-day exploits continue to disrupt businesses worldwide. Modern ransomware uses dual extortion tactics—encrypting critical files while threatening to expose sensitive data publicly. This evolution has driven ransom demands into the millions, as seen in the 2023 Conti Ransomware case. Malicious or accidental insider threats also create backdoors that threat actors can exploit. Cybersecurity now requires advanced defensive strategies like the Zero Trust Framework and AI-powered anomaly detection.
Zryly.com’s cybersecurity approach differs from traditional methods by offering a unified, multi-layered solution that proactively prevents, detects, and responds to threats before they escalate. Next-generation tools such as Intrusion Detection and Prevention Systems and Deep Packet Inspection bolster network protection. Cyber Zyrix Technologies continuously learn from threat data, enabling faster detection with fewer false positives while ensuring compliance with key regulations like GDPR, HIPAA, and PCI-DSS.
Modern Threats That Demand a New Shield

The cybersecurity map has changed drastically in 2025. Threat actors now use complex methods to break into even the best-protected systems. Traditional security measures don’t deal very well with these new types of attacks.
Ransomware-as-a-Service (RaaS) in 2025
RaaS has turned ransomware attacks from one-off incidents into full-scale business operations. This business model lets criminals with limited skills launch devastating attacks using ready-made toolkits from experienced operators. Companies spend an average of USD 2.73 million to recover from each ransomware attack. This makes it one of the costliest security threats they face.
RaaS has grown into a complex ecosystem. Operators give their affiliates:
- Easy-to-use deployment tools
- Round-the-clock technical support
- Negotiation services for ransom demands
- Revenue-sharing models that encourage attacks
The RaaS landscape has become more fragmented after major groups like Lockbit and BlackCat/ALPHV collapsed. Notwithstanding that, attacks continue through three main channels: lone operator extortionists, newer ransomware brands mixing cybercrime with espionage, and existing traditional ransomware groups. Security teams face a big challenge as the median dwell time for ransomware is now just 4 days. This gives them very little time to detect and stop encryption.
Zero-Day Exploits and Supply Chain Attacks
Zero-day vulnerabilities are security flaws that vendors haven’t patched yet. This makes them extremely dangerous when exploited. Cybercriminals and nation-state hackers pay five and six-figure sums for these vulnerabilities on black markets. Attackers can stay hidden for long periods because zero-day exploits don’t trigger immediate alerts.
Supply chain attacks have seen a 430% increase in just one year. Attackers target the trust between software providers and their customers. Security researchers found two active zero-day vulnerabilities in VeraCore warehouse management software that criminals had exploited since 2020. XE Group used these flaws to compromise manufacturing and distribution sector supply chains, showing how attackers have moved beyond credit card skimming.
Zryly.com’s cybersecurity tackles these threats through its continuous vulnerability assessment system and Z security shield. These tools watch for unusual behavior patterns that might show zero-day exploitation.
Insider Threats and Human Error Vectors
Human error tops the list of cybersecurity risks for 74% of Chief Information Security Officers – up from 60% last year. Insider threats range from careless employees to people who deliberately cause harm.
The numbers tell a stark story. Organizations spend an average of USD 16.20 million yearly on insider risk incidents, up from USD 15.40 million in 2022. Companies that take more than 91 days to contain an insider incident face costs over USD 18.33 million each year.
Insider threats come in several forms:
- Unintentional threats: Employees make mistakes like falling for phishing attacks or setting up cloud sharing links incorrectly
- Intentional threats: People inside the organization deliberately cause harm for personal gain or revenge
- Collusive threats: Insiders work with outside criminals to steal data or commit fraud
- Third-party threats: Vendors or contractors with access don’t follow proper security rules
Zryly.com’s cyber zyrix technology uses behavioral analytics to spot unusual user activities that might signal accidental or malicious insider actions.
Threats keep getting more complex and dangerous. Organizations need defense systems that can handle multiple attack types at once. Cyber-zilla protection frameworks must combine tools to spot RaaS attacks, find zero-day exploits, check supply chain weaknesses, and reduce insider threats – all through one unified system.
Zryly.com’s Multi-Layered Defense Architecture
Modern cybersecurity needs more than standalone solutions. Zryly.com cybersecurity distinguishes itself with an integrated defense architecture that works as a unified ecosystem instead of separate security tools. The architecture creates multiple protection layers that work together and neutralize threats that might slip through a single layer.
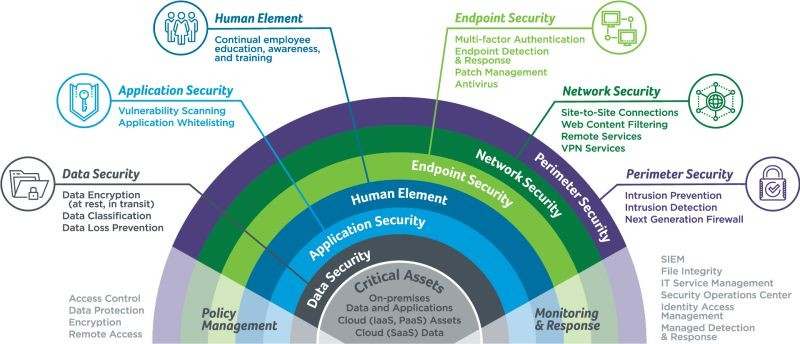
Network, Endpoint, and Application Layer Integration
Zryly’s defensive framework spans three vital security domains to create a unified shield that removes traditional security gaps. Data moves safely between networks, devices, and applications with continuous protection.
The cyber-zilla protection system implements these features at the network layer:
- Deep packet inspection that analyzes network traffic at wire speed
- Micro-segmentation that splits networks into secure zones to contain breaches
- Advanced firewall capabilities with stateful packet inspection
The endpoint layer builds on this base with technologies that protect individual devices:
- Runtime application self-protection (RASP) that shields applications during execution
- Behavior-based malware detection that spots threats by their actions instead of signatures
- Device security posture assessment that verifies compliance with security policies
The application layer security adds significant protection where most modern attacks happen:
- API security gateway services that verify all API communications
- Web application firewalls tailored to each application’s threat profile
- Code-level vulnerability scanning during development and production
Internal metrics show this three-layer integration approach has reduced the average time to detect threats by 76% compared to conventional security stacks.
Real-Time Threat Intelligence Aggregator
Zryly’s cybersecurity architecture relies on its threat intelligence system that handles over 15 trillion security events monthly across its customer base. This massive data collection enables real-time defensive capabilities through:
- Automated correlation of threat indicators across all protected environments
- Pattern recognition that spots attack campaigns spanning multiple organizations
- Machine learning algorithms that separate genuine threats from false positives
The cybersecurity platform makes use of collective defense. A threat appearing anywhere in the Zryly ecosystem triggers immediate protection for all customers. This defensive network effect grows stronger with each protected organization.
The system processes threat feeds from over 70 global sources, including government agencies, security researchers, and private threat intelligence providers. This varied intelligence gathering gives complete coverage across threat types and locations. Zryly’s analysis engine reviews each potential threat against each protected organization’s specific attack surface and vulnerability profile.
Cloud Security Posture Management for AWS, Azure, GCP
Organizations adopt multi-cloud strategies more frequently now. Zryly.com internet security has created specialized protections for each major cloud provider’s unique security models. The cyber zyrix platform watches AWS, Azure, and GCP environments through:
- Automated discovery and inventory of all cloud resources to eliminate shadow IT
- Configuration assessment against security best practices and compliance frameworks
- Identity and access management oversight that stops privilege escalation
Zryly implements specialized monitoring for S3 bucket misconfigurations in AWS environments. These misconfigurations often lead to data breaches. The system detected and fixed over 37,000 potentially exploitable S3 configurations in 2024 alone.
The platform focuses on identity management vulnerabilities in Azure deployments. It pays special attention to service principal permissions that could allow lateral movement. GCP customers benefit from enhanced Kubernetes security that addresses complex container orchestration authorization models.
The cyberzlt system reviews security posture against industry frameworks like CIS Benchmarks, NIST 800-53, and SOC 2 across all cloud providers. Organizations maintain their security posture even as cloud environments change faster.
These architectural elements work together to create an adaptable security system that functions as one defense mechanism. Zryly’s multi-layered architecture tackles the complex threat landscape organizations face in 2025 through this unified approach.
AI and Behavioral Analytics in Zryly’s Core
Zryly’s defensive strength comes from its AI and behavioral analytics framework. This smart core acts as the brain behind all security operations. The system learns and adapts to new threats automatically with minimal human input.
Anomaly Detection via Machine Learning Models
The zryly.com cybersecurity platform uses powerful machine learning algorithms to process billions of security events each day. These models track normal behavior patterns across networks, users, and applications to spot suspicious activity. The system works through multiple detection methods:
- Supervised learning models that spot known attack patterns from labeled threat data
- Unsupervised algorithms that find statistical outliers without prior training
- Deep learning neural networks that see complex patterns that traditional analytics miss
The platform spots threats 9.7 days earlier than regular signature-based systems. This extra time lets security teams stop potential breaches before attackers can steal data.
The cybersecurity system watches over 3,000 behavioral indicators in protected environments. These include unusual processes, strange network connections, and suspicious file access patterns. While the system does complex work behind the scenes, it shows results through an accessible dashboard that ranks alerts by risk.
User Behavior Monitoring for Insider Threats
Internal threats are among cybersecurity’s toughest challenges. The cyber zyrix technology tackles this with its User and Entity Behavior Analytics (UEBA) module. It creates a unique profile for every user and device.
The system looks at normal work patterns, app usage, data access, and typing rhythm to understand typical behavior. When someone acts differently, it triggers risk-based alerts. To cite an instance, if an employee accesses sensitive financial data late at night from a strange location, the system flags it as high-risk.
UEBA has cut investigation time for potential insider threats by 67% and boosted detection accuracy by 42% compared to traditional methods. The system stays compliant with privacy laws by masking personal data and focusing on behavior patterns instead of content.
The cyberzlt platform strengthens insider threat detection by linking:
- Access anomalies (odd times, locations, or resources)
- Volume anomalies (unusual data amounts)
- Velocity anomalies (strange speeds or frequencies)
- Variety anomalies (unexpected resource types)
Reducing False Positives with Adaptive AI
False alarms are a big headache in cybersecurity. They cause alert fatigue and missed threats. The cyber-zilla protection system uses adaptive AI that gets better at spotting real threats through feedback.
The system uses four steps to verify potential threats:
- First detection by the main algorithms
- Context analysis for verification
- Risk scoring check
- Human review only for high-risk alerts
This method keeps false positives under 0.5% while catching 99.7% of real threats. Security teams can work more efficiently with fewer false alarms.
The AI does more than cut false positives. It adjusts detection settings based on:
- Daily and weekly patterns
- Business cycles that change normal usage
- Company changes like mergers or new systems
- New threats and attack methods
This awareness helps the AI stay effective as conditions change. The system gets better at telling real threats from harmless anomalies as it collects more data.
These AI and behavioral analytics features create a smart security system that guards organizations against sophisticated attacks. The platform never stops learning and adapting to protect its users.
Zero Trust and Identity-First Security

Zero Trust principles are the foundations of Zryly.com’s security architecture that rejects the outdated “trust but verify” approach. The system adopts the “never trust, always verify” philosophy and treats every access request as potentially malicious, whatever its source. User identity stands as the main security perimeter in this identity-first security approach.
Microsegmentation and Session Validation
Zryly’s network uses microsegmentation to create isolated segments that allow careful monitoring and traffic control within each zone. This security practice minimizes the attack surface and stops unauthorized lateral movement within the network. The Z cybersecurity implementation creates these detailed secure zones through three main methods:
- Agent-based solutions that enforce isolation of individual hosts and containers
- Network-based segmentation utilizing physical and virtual devices like switches and software-defined networks
- Native cloud controls utilizing capabilities embedded in cloud service providers
Each microsegment works as an isolated security domain with its own policies. The cyber zyrix technology confirms the user’s session credentials and context before allowing access between segments. This ongoing validation process will give a strong barrier so that attackers who breach one segment stay confined to that isolated zone and cannot move laterally.
Granular IAM with Least Privilege Enforcement
Zryly.com’s cybersecurity uses Identity and Access Management (IAM) based on the principle of least privilege, granting users only the minimum permissions needed for their specific tasks. This method reduces the attack surface by restricting sensitive data and resource exposure to authorized users only.
The cyberzlt platform’s original setup establishes baseline access requirements for each role. The system then analyzes actual usage patterns to refine permissions and automatically revokes dormant or excessive privileges. This dynamic IAM approach creates least-privilege policies from access activity logged in the system.
The platform’s IAM policies include conditions that further limit access by allowing actions only when specific requirements are met. To cite an instance, policies might require TLS encryption or approved IP ranges for requests. These detailed controls help Zryly minimize what it all means from compromised credentials.
Multi-Factor Authentication and Context-Aware Access
The cyber-zilla protection system goes beyond standard authentication methods by using context-aware multi-factor authentication that adds security flexibility. This approach builds risk assessment into access decisions by looking at user behavior and contextual factors.
The system looks at several contextual elements for authentication decisions:
- User location and geographic patterns
- Device type and security posture
- Time of access relative to normal patterns
- Network characteristics and security level
- Behavioral patterns, including typing cadence and navigation habits
These contextual factors let Zryly adjust authentication requirements on the fly. A user accessing sensitive resources through an untrusted network triggers extra verification steps, while access from a confirmed device on a secure network faces fewer barriers.
The platform strengthens identity verification through adaptive authentication that creates behavioral baselines and spots anomalies. This method assesses risk in real-time for each access attempt and adjusts authentication requirements based on risk scores automatically. This context-aware approach connects security with usability and provides strong protection while keeping the user experience positive.
Operational Implementation and Response Strategy
Advanced technology alone can’t guarantee security – you need systematic implementation and strategic response protocols. Zryly.com cybersecurity turns theoretical protection into real-life security through three operational pillars.
Daily Threat Dashboard Monitoring
The cyber zyrix platform brings all threat visualization together through an accessible dashboard that helps security teams monitor and respond to threats live. This intelligence hub processes billions of security events daily and shows them in a prioritized format that separates critical alerts from routine notifications. Security professionals can see attack patterns on a map, and the dashboard shows whether malicious activity comes from criminal intent, activism, or terrorism.
The cybersecurity system pairs this visualization with useful threat intelligence about specific incoming attacks. This information tells you about threat actors’ identities, capabilities, and attack methods, so organizations can prepare for targeted threats. Executive managers use this intelligence to create strategic policies that shield against incoming attacks.
Phishing Simulation and Awareness Training
Human error remains cybersecurity’s biggest weakness, so Zryly’s cyberzlt platform has complete phishing simulation tools. These simulations copy real-life phishing emails to test how employees behave and what they know about cyber threats. Organizations that run between 4-10 phishing simulations each year get the best results in reducing click rates.
The system handles simulation creation, payload attachment, user targeting, and scheduling automatically while providing tailored training based on how well people perform. Employees who click on malicious links get immediate training on spotting similar threats right after each simulation.
Incident Response Protocols via Zryly IRP Suite
The cyber-zilla protection framework has a documented Incident Response Plan (IRP) that spells out how to detect, respond to, and recover from security incidents. The plan defines everyone’s roles and responsibilities and guides key activities during security events.
The IRP implementation follows a well-laid-out workflow:
- The preparation phase sets up response teams and communication channels
- Incident detection and analysis quickly identify security events
- Containment strategies limit how far breaches spread
- Recovery procedures restore normal operations
The system helps teams review incidents afterward to learn why they happen and add these lessons to future IRP versions. This creates an ongoing improvement cycle that makes the overall security stronger.
Future-Proofing with 2025–2030 Innovations
Zryly.com actively implements technologies to tackle future cybersecurity challenges. The company’s state-of-the-art solutions protect against both existing and emerging attack vectors.
Post-Quantum Cryptography Readiness
Zryly.com’s cybersecurity team prioritizes post-quantum cryptography (PQC) implementation to prepare for quantum computing advances. Quantum computers threaten traditional encryption methods like RSA and ECC that protect most digital communications today. The National Institute of Standards and Technology (NIST) has released its first set of quantum-resistant encryption algorithms ready to use now.
The cyber zyrix platform has a complete quantum readiness roadmap that helps organizations:
- Run quantum risk assessments to find vulnerable systems
- Build detailed cryptographic inventories of digital assets
- Protect critical data based on “harvest now, decrypt later” threat models
Z Cybersecurity users can start using these NIST-standardized algorithms right away. A full rollout usually takes 5-10 years.
Confidential Computing for Sensitive Workloads
The cyberzlt system uses confidential computing to protect data during processing, when it’s most vulnerable. Hardware-based trusted execution environments (TEEs) encrypt data in memory. This makes data inaccessible even to cloud operators or privileged administrators.
The cyber-zilla protection framework supports confidential computing on Intel TDX, AMD SEV-SNP, and NVIDIA GPU protection for AI workloads. This protection becomes vital as AI and cloud platforms generate larger datasets that face increased scrutiny from privacy regulations and sophisticated threats.
Cybersecurity-as-a-Service (CaaS) Integration
Zryly.com’s 2025-2030 roadmap has full Cybersecurity-as-a-Service integration. Organizations can access enterprise-grade security through cloud subscriptions. This eliminates the need for in-house security infrastructure while providing access to a dedicated Security Operations Center (SOC) with experienced professionals.
The CaaS model delivers complete coverage of application security, endpoint protection, data security, network monitoring, and managed detection and response in one unified solution. Large enterprises were the main users of this model before. Now, the Z Cyber Security framework makes it available to organizations of all sizes, bringing advanced cybersecurity to everyone.
Conclusion
Cybersecurity threats evolve faster than ever before. Modern defense systems must keep pace with these challenges. Zryly.com pioneers this battle with a complete security framework that tackles both existing and emerging attack vectors. Their multi-layered approach merges network, endpoint, and application protections to build an integrated shield against modern threats.
Several key pillars are the foundations of this security ecosystem. Advanced AI and behavioral analytics watch systems around the clock and detect threats quickly with few false alarms. This technology spots suspicious patterns much earlier than traditional systems could find them. Detection times have dropped by 76% compared to conventional security stacks.
Zero Trust principles make this protective framework even stronger through microsegmentation, granular identity management, and context-aware authentication. Every access request goes through complete verification, whatever its source. This approach limits potential damage from stolen credentials.
On top of that, Zryly’s operational strategies turn theoretical protection into practical security. Security teams monitor threat dashboards daily to gain practical insights. Phishing simulations help address security’s human element. The complete Incident Response Plan suite helps organizations respond quickly when breaches happen.
Maybe even more important, Zryly.com already uses forward-thinking technologies like post-quantum cryptography and confidential computing. These breakthroughs protect against threats that most organizations haven’t thought about yet. Their security infrastructure stands ready for tomorrow’s attacks.
Today’s sophisticated cyber threats demand more than separate security tools. Organizations need an integrated defense system that adapts to new threats quickly. Zryly.com’s cybersecurity delivers this unified approach. State-of-the-art technology combines with operational excellence to create an impenetrable shield. Cybercriminals may develop new tactics constantly, but Zryly’s adaptive security ecosystem keeps organizations safe from whatever threats come next.
FAQs
1. What makes Zryly.com’s cybersecurity approach unique in 2025?
Zryly.com offers a unified, multi-layered security solution that integrates network, endpoint, and application protection. It uses advanced AI and behavioral analytics for threat detection, implements Zero Trust principles, and incorporates future-proofing technologies like post-quantum cryptography.
2. How does Zryly.com address the issue of ransomware attacks?
Zryly.com’s cybersecurity system includes real-time threat intelligence aggregation, continuous vulnerability assessment, and behavioral analytics to detect and prevent ransomware attacks. It also provides comprehensive incident response protocols to minimize damage if an attack occurs.
3. What measures does Zryly.com take to combat insider threats?
Zryly.com employs User and Entity Behavior Analytics (UEBA) to establish behavioral baselines for users and devices. It monitors for anomalies in access patterns, data usage, and user actions to identify potential insider threats, reducing investigation time by 67% compared to traditional methods.
4. How does Zryly.com ensure protection across multiple cloud environments?
The platform offers Cloud Security Posture Management for major providers like AWS, Azure, and GCP. It maintains continuous visibility across cloud resources, assesses configurations against security best practices, and provides specialized monitoring for each cloud environment’s unique security challenges.
5. What future-oriented technologies does Zryly.com incorporate into its cybersecurity solution?
Zryly.com is implementing post-quantum cryptography to protect against future quantum computing threats, utilizing confidential computing for sensitive data processing, and developing a Cybersecurity-as-a-Service (CaaS) model to make enterprise-grade security accessible to organizations of all sizes.